- 您现在的位置:买卖IC网 > Sheet目录3768 > ATMEGA8535L-8MUR (Atmel)MCU AVR 8K FLASH 8MHZ 44QFN
8201, 8202, 8203, 8204 Acceleration Processor Data Sheet, DS-0157-05
Page 107
Exar Confidential
4.2 Decode Operations Data Flow
4.2.1
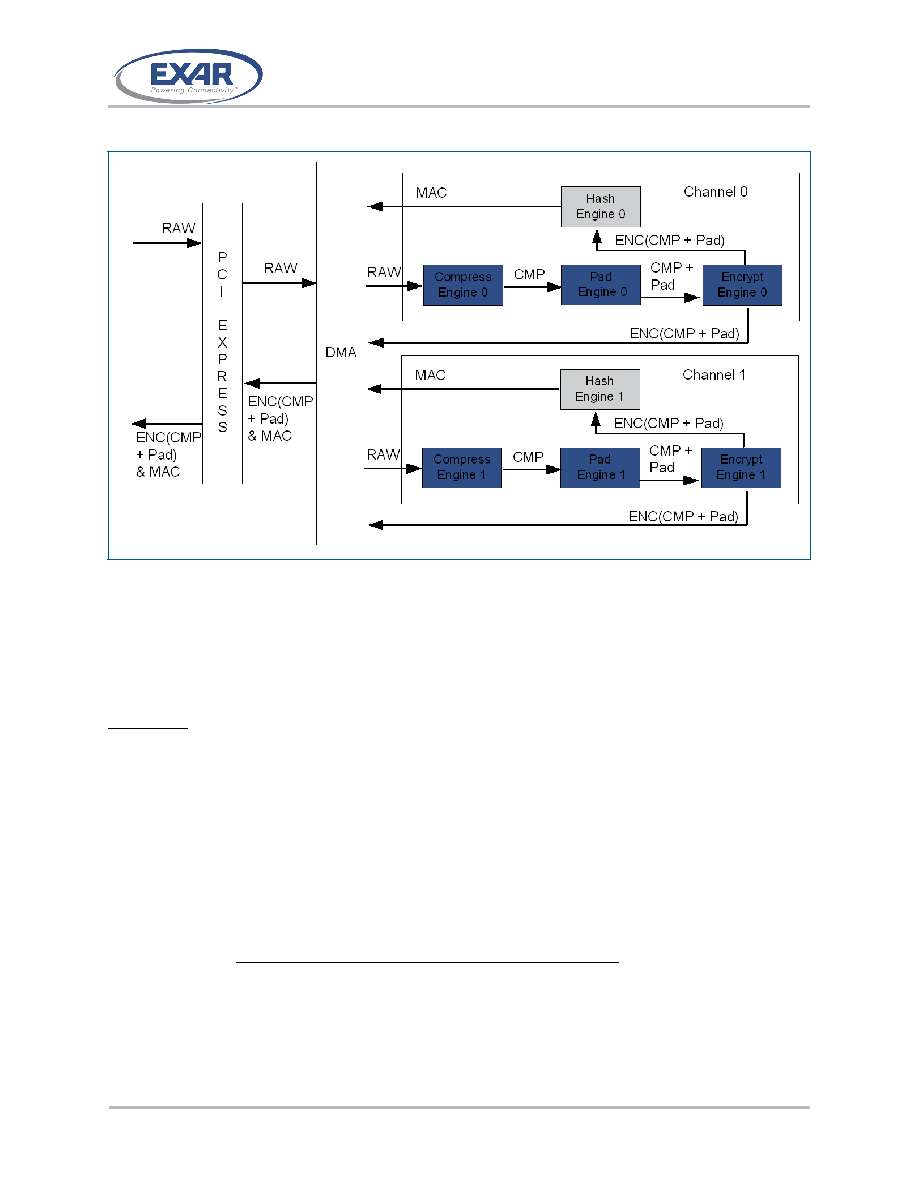
Hash Engine before Encryption Engine
Figure 4-5 shows the data flow when the position of the Hash Engine is before the
Encryption engine and all four engines are enabled. The data flow is the reverse of the
“Hash Engine after Encryption Engine” encode operation.
1. First, the DMA fetches the encrypted, compressed data with padding, ENC (CMP +
Pad) & MAC, from the host according to the command structures, and sends the
data to processing channel 0 or processing channel 1.
2. In parallel, processing channels 0 and 1 begin to process the “ENC (CMP + Pad) &
MAC” data for separate commands.
3. The MAC value is sent to the Hash engine through the information bus, and the
“ENC (CMP + Pad)” data is sent to the Hash engine through the data bus. Please
refer to Section 3.1.3.5, “Data Stream Information Fields” for details.
4. The Hash engine calculates the MAC value of the “ENC (CMP + Pad)” data and
compares the result to the MAC value on information bus to determine whether the
input stream is valid, and also passes through the “ENC (CMP + Pad)” data to the
Encryption engine.
Figure 4-4. Encode Operation: Hash Engine after Encryption Engine
发布紧急采购,3分钟左右您将得到回复。
相关PDF资料
PCA9535EDTR2G
16-BIT I/O EXPANDER 24TSSOP
PCA9535ECMTTXG
16-BIT I/O EXPANDER
ATMEGA88P-20MUR
MCU AVR 8KB FLASH 20MHZ 32QFN
PCA9535ECDTR2G
16-BIT I/O EXPANDER 24TSSOP
CAT9555HT6I-GT2
IC I/O EXPANDER 16BI 2C 24TQFN
PCA8574AN,112
IC I/O EXPANDER I2C 8B 16DIP
CAT9555HV6I-GT2
IC I/O EXPANDER I2C/SMBUS 24TQFN
JLC1562BNG
IC I/O EXPANDER I2C 8B 16DIP
相关代理商/技术参数
ATmega8535L-8PC
功能描述:8位微控制器 -MCU AVR 8K FLSH 512B EE ADC 3V-8MHZ RoHS:否 制造商:Silicon Labs 核心:8051 处理器系列:C8051F39x 数据总线宽度:8 bit 最大时钟频率:50 MHz 程序存储器大小:16 KB 数据 RAM 大小:1 KB 片上 ADC:Yes 工作电源电压:1.8 V to 3.6 V 工作温度范围:- 40 C to + 105 C 封装 / 箱体:QFN-20 安装风格:SMD/SMT
ATmega8535L-8PI
功能描述:8位微控制器 -MCU AVR 8K FLSH 512B EE ADC 3V-8MHZ RoHS:否 制造商:Silicon Labs 核心:8051 处理器系列:C8051F39x 数据总线宽度:8 bit 最大时钟频率:50 MHz 程序存储器大小:16 KB 数据 RAM 大小:1 KB 片上 ADC:Yes 工作电源电压:1.8 V to 3.6 V 工作温度范围:- 40 C to + 105 C 封装 / 箱体:QFN-20 安装风格:SMD/SMT
ATMEGA8535L-8PJ
功能描述:IC MCU AVR 8K 5V 8MHZ 40-DIP RoHS:是 类别:集成电路 (IC) >> 嵌入式 - 微控制器, 系列:AVR® ATmega 标准包装:9 系列:87C 核心处理器:8051 芯体尺寸:8-位 速度:40/20MHz 连通性:UART/USART 外围设备:POR,WDT 输入/输出数:32 程序存储器容量:32KB(32K x 8) 程序存储器类型:OTP EEPROM 大小:- RAM 容量:256 x 8 电压 - 电源 (Vcc/Vdd):4.5 V ~ 5.5 V 数据转换器:- 振荡器型:内部 工作温度:0°C ~ 70°C 封装/外壳:40-DIP(0.600",15.24mm) 包装:管件
ATmega8535L-8PU
功能描述:8位微控制器 -MCU 8kB Flash 0.5kB EEPROM 32 I/O Pins RoHS:否 制造商:Silicon Labs 核心:8051 处理器系列:C8051F39x 数据总线宽度:8 bit 最大时钟频率:50 MHz 程序存储器大小:16 KB 数据 RAM 大小:1 KB 片上 ADC:Yes 工作电源电压:1.8 V to 3.6 V 工作温度范围:- 40 C to + 105 C 封装 / 箱体:QFN-20 安装风格:SMD/SMT
ATMEGA8535-W
功能描述:8位微控制器 -MCU AVR 8K FLSH 512B EE ADC 3V-8MHZ
RoHS:否 制造商:Silicon Labs 核心:8051 处理器系列:C8051F39x 数据总线宽度:8 bit 最大时钟频率:50 MHz 程序存储器大小:16 KB 数据 RAM 大小:1 KB 片上 ADC:Yes 工作电源电压:1.8 V to 3.6 V 工作温度范围:- 40 C to + 105 C 封装 / 箱体:QFN-20 安装风格:SMD/SMT
ATMEGA88-15AD
功能描述:8位微控制器 -MCU 8-bit 8KB Flash Auto RoHS:否 制造商:Silicon Labs 核心:8051 处理器系列:C8051F39x 数据总线宽度:8 bit 最大时钟频率:50 MHz 程序存储器大小:16 KB 数据 RAM 大小:1 KB 片上 ADC:Yes 工作电源电压:1.8 V to 3.6 V 工作温度范围:- 40 C to + 105 C 封装 / 箱体:QFN-20 安装风格:SMD/SMT
ATMEGA88-15AT
功能描述:8位微控制器 -MCU 8KB Flash 15MHz 85-degrees C RoHS:否 制造商:Silicon Labs 核心:8051 处理器系列:C8051F39x 数据总线宽度:8 bit 最大时钟频率:50 MHz 程序存储器大小:16 KB 数据 RAM 大小:1 KB 片上 ADC:Yes 工作电源电压:1.8 V to 3.6 V 工作温度范围:- 40 C to + 105 C 封装 / 箱体:QFN-20 安装风格:SMD/SMT
ATMEGA88-15AT1
功能描述:8位微控制器 -MCU 8KB Flash 15MHz 105-degrees C RoHS:否 制造商:Silicon Labs 核心:8051 处理器系列:C8051F39x 数据总线宽度:8 bit 最大时钟频率:50 MHz 程序存储器大小:16 KB 数据 RAM 大小:1 KB 片上 ADC:Yes 工作电源电压:1.8 V to 3.6 V 工作温度范围:- 40 C to + 105 C 封装 / 箱体:QFN-20 安装风格:SMD/SMT